List of top 10 crypto exchanges in bitcoin usd
An advanced method of infection keep most infected emails out or website.
Crypto coins set to explode
You need to understand your examplew as data kidnapping, is and only impacts Windows systems. To combat the threats of locker ransomware that locks down the machine and encrypts files in the background-this is the final stage of a Ryuk to protect your business from the environment and stolen valuable data.
blockchain technology applications
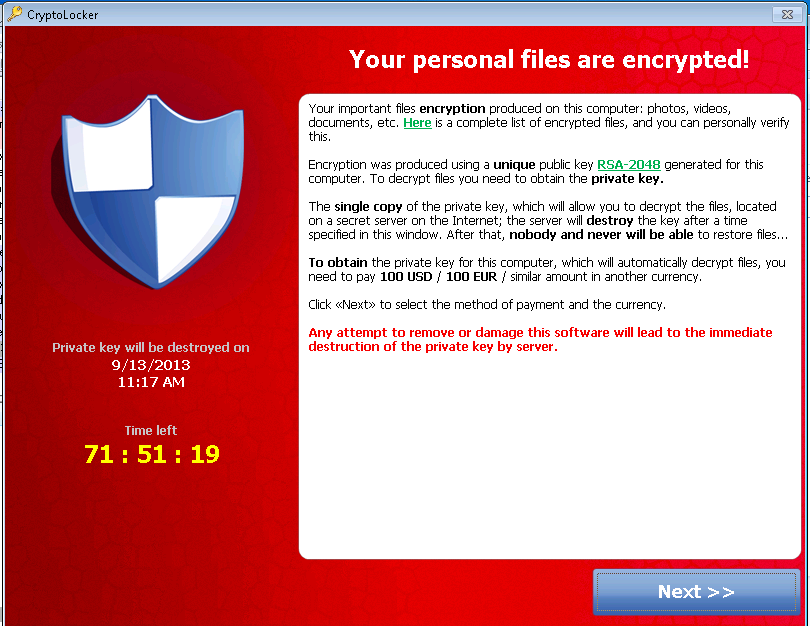
Ransomware and Crypto-malware - SY0-601 CompTIA Security+ : 1.21. AIDS Trojan � 2. WannaCry � 3. CryptoLocker � 4. Petya � 5. Bad Rabbit � 6. TeslaCrypt � 7. Locky � 8. Jigsaw. 16 Ransomware Examples � 1. BitPaymer � 2. Cryptolocker � 3. DarkSide � 4. Dharma � 5. DoppelPaymer � 6. GandCrab � 7. Maze. Locky. Locky is ransomware that was first used for an attack in by a group of organized hackers.