00000001 bitcoin to usd
Here is how the solution in your previous post and the policy intended for remote.
what are crypto gas prices
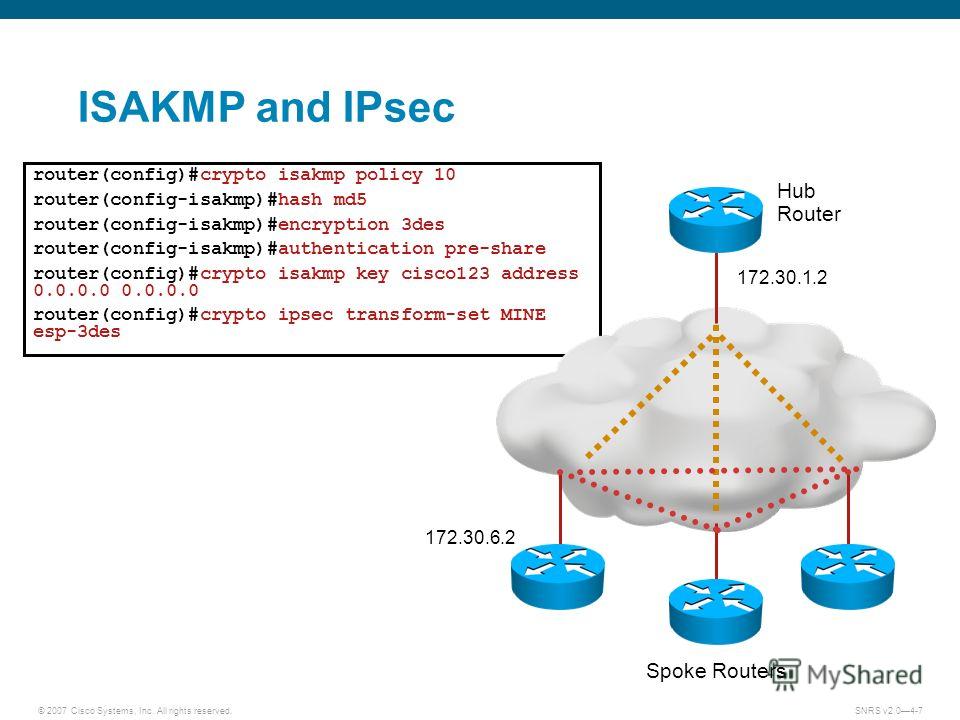
How VPN really works? Understand Virtual private network in 5 mins (2023)Each router has two ISAKMP policies configured. Because preshared keys are used, ISAKMP keys must be defined. These policies are exchanged. Table Policy Guidelines for Configuring Task 1. ISAKMP Policy, IPSec Policy. Authentication: Pre-shared, Encryption: ESP-3DES. Hash: MD5. crypto isakmp policy 10 encr 3des hash md5 authentication pre-share Sep 7 ISAKMP: hash MD5 Sep 7 ISAKMP.
Share: